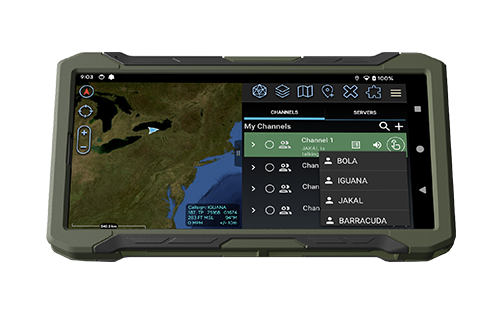
Face It, Warfighters Need an Intuitive User Interface
Technology developers must strike a balance between an interface that is visually appealing and one that’s functional. A user interface is a gateway — it’s a visual path to information or functionality that results in an experience. Warfighters need a clear and concise interface to give them clear and concise direction that isn’t cluttered by unnecessary options.
The Security Triad

Many sources equate secure communications to encryption. While encryption certainly plays a key role in a secure communications solution, it is not the only required element. The cybersecurity industry uses a model referred to as the security triad to define the various domains that need to be addressed when securing a network. The triad – sometimes also known as CIA – includes Confidentiality, Integrity, and Availability. This paper will review and define these domains for a better understanding of what is required to provide a complete secure communications solution.
Thwarting Cyber Attacks with Honeypot System for Sigma

Every device that carries information is worth hacking – even if the device operates behind firewalls, intrusion detection systems, or session border controllers. At REDCOM, we develop secure VoIP platforms that are intended to withstand harsh cyber environments without the protection provided by typical front-facing equipment.
REDCOM at the Ready: Hardening communications for EMP protection
The President signed an Executive Order directing the Federal government to prepare the United States for an EMP (Electromagnetic Pulse) attack by hardening critical infrastructure as much as possible. After almost 20 years of studies, the Federal government is starting to pay attention and REDCOM is taking action.
What is UX Design and Why is it Good for Product Design at REDCOM?
Lately, there has been a lot of talk in the media about User Experience when it comes to the design of products. This is true of both physical goods like telephones or cars and digital interfaces like websites and software. So, you may find yourself asking, “what exactly is UX, and why is someone’s ‘experience’ important?” REDCOM’s UX Specialist, Jim Parrillo explains UX design, and why it’s necessary for product design at REDCOM.
Army budget request adds $1.5B for network modernization

The U.S. Army will be making large investments in network modernization over the next five years. Network modernization is one of the Army’s top priorities as they seek to enhance their ability to fight and win against near peer adversaries.
Protect your intellectual property by partnering with the right U.S.-based manufacturer

Selecting the right contract manufacturing partner can make or break your business, especially if there’s the potential for your intellectual property to fall into the wrong hands. REDCOM EMS can mitigate these problems with our secure, NIST-compliant manufacturing facility located in western New York state. Not only do we manufacture domestically, but we also keep all of our sales, service, engineering, and project managers on-site as well. Protect your intellectual property and trade secrets by partnering with a trusted CM such as REDCOM EMS.
Who Salted my Hash?

It seems that every week lately there is a story on the evening news about a database that has been breached and a warning issued that hackers may have your login credentials. Network information security doesn’t appear to be too healthy. One ingredient that can be used to improve the health of the system is salt. Believe it or not, salt can actually help to improve the health of information security.
Alaskan Code Talkers – Bringing Secure Communications to WWII

Code Talkers played a critical role in our ability to command and control forces in the Pacific during World War II, maintaining secure communications and outsmarting our enemies. REDCOM prides itself of providing the most secure communications in the world and protecting the most important conversations. We respect and honor these men for doing the same.
SWaP – It’s bigger than ‘the box’

When most people think about low SWaP, they tend to focus solely on the size of the box itself, without thinking about everything that comes with it. In this post, we will take a more holistic approach to Low SWaP and address things such as batteries, generators, peripherals, transportation, and support personnel.
Looks can be deceiving, and the size of any given device is only a small part of the big picture.