Response to: Catastrophic disasters could hit millions of Americans in the coming years. What can the Army do?

A recent article published in the ArmyTimes highlights the requirements of the Army and Army entities in the aftermath of domestic catastrophic incidents but fails to touch on the importance of re-establishing communications.
How REDCOM Secures the Mission Part 1: Technology

REDCOM takes a holistic, multi-layer approach to security that goes beyond typical measures such as encryption and validation. Here we address REDCOM’s stance on overall mission security, which necessitates a strong focus on encryption.
Russia’s Large, Unique Presence in the Landscape of Cyber Warfare

In current American discourse surrounding cybersecurity, we are often confronted with the idea of the Russian adversary. Whether it be botnets, malware attacks, network intrusions, or general disinformation, many are quick to pin malicious cyber activity on Russian operators. Following our 2016 presidential election, Russia’s influence in this realm became apparent, even to those not well-versed in cyber-threat analysis. Before this though, experts have known not only of Russia’s deep involvement in cyber-warfare, but also of the peculiar geopolitics that put Russia in a unique position within the international cyber-landscape.
FIPS 140-2: Validation versus Compliance
When considering products or services for handling an agency’s information, it is common to see two variations of FIPS accreditation: FIPS validated and FIPS compliant. Although they seem similar, there are different implications with these two labels.
To speed up disaster relief, restoring communications should be a priority

Natural disasters like Hurricane Dorian are increasing in severity and frequency. Dorian reminds us yet again of the need for us all to be prepared for the worst. When a disaster of this magnitude strikes, it often knocks out the power grid and communications infrastructure. Without the ability to communicate, everything suffers: relief coordination efforts, medical evacuations, and the resupply of food and water. To speed up disaster relief, it is imperative that we make restoring communications a priority.
FIPS 140-3: What you need to know
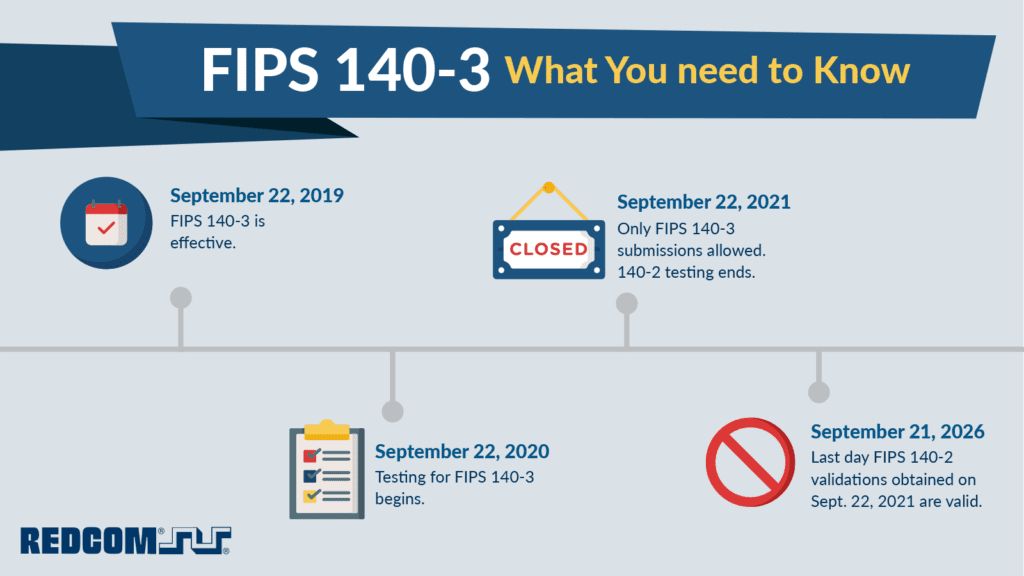
REDCOM is aware of what needs to be done to keep up to date with all security protocols. So, what do you need to know in order to begin the FIPS 140-3 validation process? We’ve got it all mapped out for you.
Equivalencies in Security
When in an online environment, many utilize encryption to protect their communications and personal data. Any encryption method will make data inherently safer than letting it remain unencrypted. How could one make an informed decision as to which cryptographic technique is right for them? We can turn to bits of security – a hypothetical measure of an encryption’s functional strength.
Face It, Warfighters Need an Intuitive User Interface
Technology developers must strike a balance between an interface that is visually appealing and one that’s functional. A user interface is a gateway — it’s a visual path to information or functionality that results in an experience. Warfighters need a clear and concise interface to give them clear and concise direction that isn’t cluttered by unnecessary options.
The Security Triad

Many sources equate secure communications to encryption. While encryption certainly plays a key role in a secure communications solution, it is not the only required element. The cybersecurity industry uses a model referred to as the security triad to define the various domains that need to be addressed when securing a network. The triad – sometimes also known as CIA – includes Confidentiality, Integrity, and Availability. This paper will review and define these domains for a better understanding of what is required to provide a complete secure communications solution.
Thwarting Cyber Attacks with Honeypot System for Sigma

Every device that carries information is worth hacking – even if the device operates behind firewalls, intrusion detection systems, or session border controllers. At REDCOM, we develop secure VoIP platforms that are intended to withstand harsh cyber environments without the protection provided by typical front-facing equipment.







