Zero-Knowledge Proofs and their Impact on Cyber Security

A Zero-Knowledge Proof (ZKP) is a protocol that verifies whether certain knowledge exists without revealing it. The only information verified by a ZKP is that the proving party knows the secret. The verifying party does not learn what the secret is and cannot obtain or reconstruct the secret in any form. In a world of password-based authentication and digital privacy, this could be a game-changer to modern cybersecurity.
Hypothetical Cyber Attack – Exploiting WEA
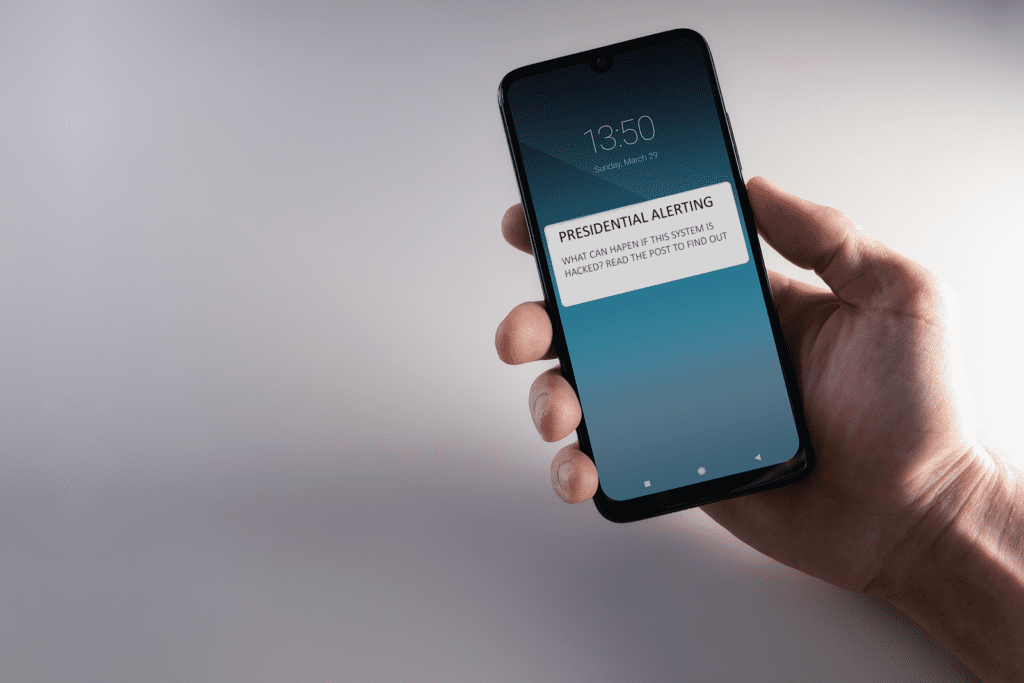
WEA is the system responsible for driving critical announcements to all available LTE devices in a target area. As an exercise, REDCOM looked at its vulnerabilities and how it can be manipulated by nefarious actors.
Communications for Humanitarian Aid

In the wake of a natural disaster, having effective communications for humanitarian aid is critical to rapid and efficient response, and the key to success.
Co-Op Feature with Conor Ahern

REDCOM routinely has co-op and internship opportunities available for college students that want to earn real-world experience at a technology company. Our engineering department finds it particularly important to bring these young engineers into the mix for their new perspectives and ideas. At REDCOM, co-op students collaborate directly with our product development teams and are often involved in truly meaningful projects.
The Reality of Tactical Communications

After 20 years of holding communicative superiority at the tactical edge over adversaries, the United States has relied on certain methods that will not be available in the next fight.
Secure Conferencing Beyond Mass-Market Software

The global pandemic has forced workers and executives across industries to transition to remote work. Many organizations need more than commercially available conferencing tools to keep their conversations secure.
What is the Army’s Network Integration Technology Enhancement (NITE) Program?

Overview of NITE (formerly called 5GTI/Inc1) NITE is an acronym for Network Integration Technology Enhancement and was formerly known as 5GTI (5th Generation Technical Insertion) Increment One. While NITE represents an essential development for the state of the Army’s tactical communications stack, it is only an element of increment one of four of the Army’s […]
Mitigation of Insider Threat Begins and Ends with Security Culture

Two of the largest data breaches in recent United States history were carried out by malicious insiders. Improving security culture by becoming proficient in the basics of security and promoting its importance within our working communities is the first and most important step toward mitigating insider threat.
Code of Honor: The Navajo Code Talkers in WWII

The Navajo Code Talkers were an elite group of men that were sent to Marine divisions stationed in the Pacific. During the first 48 hours of the Battle of Iwo Jima, they coded over 600 transmissions with impeccable accuracy and speed unmatched by coding machines.
Code of Honor: Navajo Code Talkers on Iwo Jima

Throughout the battle of Iwo Jima during WWII, Marines were able to openly send and receive encoded messages by radio or by tactical telephone thanks to the efforts of the “Navajo Code Talkers”. Were it not for the Navajos, the Marines would never have taken Iwo Jima.