The importance of low SWaP C2 for the U.S. Air Force

The United States Air Force is going all-in on Agile Combat Employment (ACE), a concept of operations that relies less on large overseas airfield “hubs” and more on smaller “spokes” —tiny, nimble airstrips that enable the Air Force to launch aircraft from anywhere and maneuver faster than ever before.
Killing the CAC

Since 1999 the Common Access Card (CAC) has been the norm for service members. The CAC has been the standard for so long that the industry has now created technology that far surpasses the CAC. The industry is moving from a net-centric to a data-centric approach. This shift is part of the call to “Kill the CAC.”
Current State of Chat at the Tactical Edge

Communications at the tactical edge are constantly evolving. During OIF, OEF, OIR, and OND, chat grew exponentially as a primary form of communication, proving its place as an essential component of the Command and Control toolkit.
JADC2 at the Tactical Edge

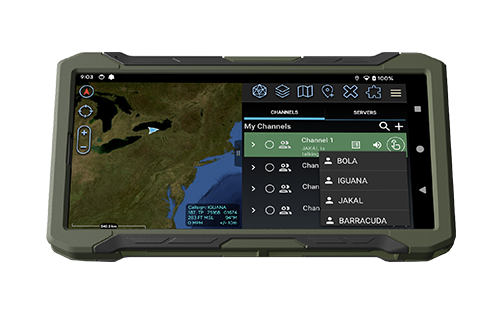
Command and Control systems are fundamental to all military operations, delivering the critical information necessary to plan, coordinate, and control forces and operations across the full range of Department of Defense (DoD) missions.
Cybersecurity and Radio Interoperability at the Tactical Edge

In today’s technological climate, cybersecurity is becoming more important to mission success by the day. As our near-peer adversaries continue to invest in cyber capabilities for protection as well as aggression, it is critical that we secure our technological assets across all echelons. Such security is equally important to both the strategic decision-maker and tactical warfighter. REDCOM Sigma XRI is designed with these considerations in mind and is rigidly purpose-built for even the most intense cyber operations.
Establishing Battlefield Superiority with Core Command and Control functions

Command and Control (C2) refers to the strategic, operational, and tactical communications systems used to manage the mission and synchronize situational awareness. Our C2 solutions include the core functionality — voice, video, and chat — required in all environments, from the network operations center out to the tactical edge.
What is CMOSS?

The U.S. Army defined a suite of open architecture standards to reduce C5ISR (command, control, computers, communications, cyber-defense, intelligence, surveillance, and reconnaissance) demands. These standards will address SWaP (System Size, Weight, and Power) requirements and provide commonality across multiple platforms by sharing hardware and software components. This architecture defines CMOSS, (C5ISR Modular Open Suite of Standards), driving a change in how hardware and software interact.
What is C5ISR?

C5ISR is an acronym for Command, Control, Computers, Communications, Cyber, Intelligence, Surveillance and Reconnaissance. REDCOM’s proven C2 solutions form the foundation for expanded C5ISR or C6ISR capabilities at the tactical edge.
What is the Zero-Trust Architecture?

After reviewing the DoD reference ZTA put forward by DISA we identified many notable trends and significant findings. In this article, we discuss our observations on the DISA Reference ZTA and posit different strategies for effectively mitigating the technical, organizational, and strategic risks associated with them.
Meeting U.S. Army future operating concepts with Sigma XRI

In the next fight, ease of use, interoperability, and integration with Joint and Coalition forces will be critical for mission success. In line with these operational concepts, REDCOM presents Sigma® XRI-400, a full-featured C2 platform that delivers voice, video, chat, and radio interoperability in a single box.