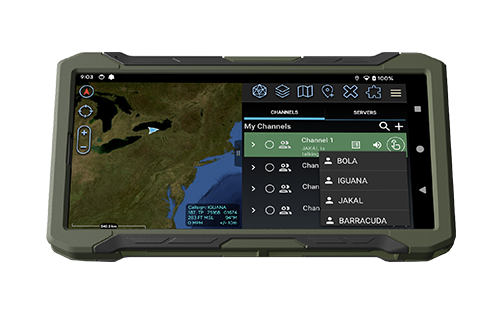
Feature-rich C2 communications console for the tactical edge and first responder networks

When developing the C2 Console, REDCOM did not adapt commercial software to the tactical environment. Rather, the Sigma C2 Console was built from the ground up with military and public safety users in mind. This means we focused on the areas most critical for the tactical domain: user experience (UX), simplicity, and scalability.
Extending C2 capabilities with REDCOM Sigma and TSM Waveform Interoperability

REDCOM® Sigma® is a unified C2 platform with voice, video, chat, conferencing, and radio interoperability in a single platform. REDCOM Sigma 3.1 introduces integrated support for radio talk groups on a TrellisWare® TSM™ Mobile Ad Hoc Network (MANET).
Are your multi-party secure comms ACC compliant?

You can communicate securely and be ACC compliant by using General Dynamics Sectéra® vIPer™ phones, however, this is only point-to-point.
If you need to conference together multiple parties anywhere in the world using ACC-compliant Type 1 encryption, then you need the REDCOM Secure Voice Gateway (SVG). The REDCOM SVG enables any number of conferees to easily communicate securely whether they are on the red side or black side of the network.
Staying Connected in Crisis: Enabling C2 Comms in a Tactical Domain

The current situation over national sovereignty in eastern Europe has the world on edge. It began with cyberattacks and is quickly evolving into kinetic warfare. The requirement for effective, stand-alone C2 comms has become more important than ever before. REDCOM can play an important role in delivering proven C2 solutions to enable communications that help defend freedom anywhere in the world.
What is a Cybersecurity Expert?
The term cybersecurity expert is overplayed. There is no official or legal definition, and between companies, the meaning of “cybersecurity expert” can vary greatly. As we talk to others, what attributes do we use to signal that we are cybersecurity experts?
Identity and Authentication: the most important pillars in a Zero Trust Architecture

The DoD document, Zero Trust Reference Architecture, is quite expansive and a bit intimidating. One of the most critical points discussed are the seven key pillars — or focus areas — to implementing a zero trust environment.
REDCOM Sigma: the C2 foundation for Army Capability sets and network modernization

Every two years the Army comes out with a new set of iterative series of integrated tactical communications packages for delivery to Soldiers. Each capability set builds on that of the previous iteration to complete the end goal of forming a multi-domain capable network by 2028.
REDCOM ZKX FAQ

In November 2021 REDCOM and AFCEA hosted a webinar where the current state of the Zero Trust Architecture at the tactical edge was discussed along with our newest solution, ZKX. We had lots of audience questions, but we weren’t able to get to them all in the allotted time. So, we decided to form this FAQ.
Zero Trust vs. Zero Knowledge

The two concepts might be similar in the name; however, they are in fact two completely different ideas. Zero-Knowledge can be used to help complete the notion of Zero Trust, but it cannot work in the opposite.
REDCOM Webinar: Zero Trust Architectures for the Tactical Edge
Watch our webinar: Zero Trust Architectures for the Tactical Edge