Closing the Gaps in CJADC2 with Communications Interoperability

While AI may be effective in analyzing and compiling data, it does not solve communication issues like interoperability between networks. By streamlining communication vertically and adjacently, information can be passed more efficiently, leading to more successful operations.
What is a PACE Plan?

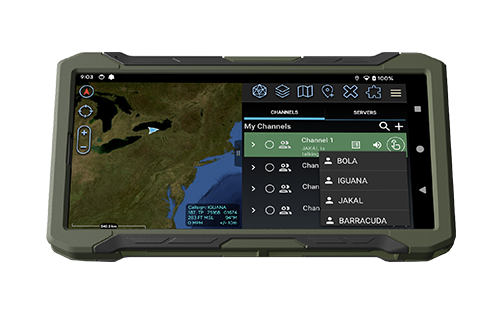
Primary, Alternative, Contingency, and Emergency (PACE) plans are crucial to mission success. To maintain readiness wherever possible, it’s vital to maximize the ability to leverage multiple pathways with systems that are already fielded to support strong PACE options, enabling uninterrupted communication down to the tactical edge. REDCOM Sigma is a complete software-based Command & Control solution that can form the core of your auto-PACE plan.
The dangers of offshoring engineering & development

Knowing where mission-critical hardware and software products are engineered and manufactured is essential to national security. When products are intended for use at the highest level of government and at the tactical edge, it is imperative that you know where these products are being sourced.
What is tactical radio interoperability?

Using multiple communications methods at the tactical edge is critical to mission success, but it also leads to interoperability challenges. As a result, a warfighter or operator in the field might not be able to connect to someone in a command post, on a vehicle, or in headquarters, unless they have matching equipment. And this matching equipment may not be mobile — or feasible.
The Virtues of REDCOM Sigma: Our Products and their Capabilities

REDCOM is committed to building the most flexible, versatile, and Low SWaP command and control communications solutions. It all starts with our flagship software product: REDCOM Sigma.
What is Interoperability?
Industries that rely on communications need interoperability. In emergencies or at the tactical edge, your device shouldn’t keep you from critical intel.
Using the GD Sectéra® vIPer™ Secure Phone for Type-1 NSA ACC-Compliant Gateways

Thanks to a collaborative effort between REDCOM and General Dynamics, organizations can now implement a new ACC-compliant integrated solution for Type 1 secure voice gateways while connecting new and legacy SCIP secure voice devices.
REDCOM Secure Voice Gateway use cases

Over the past 18 months, REDCOM has seen an uptick in requests from Federal Agencies and DoD organizations that need to replace non-compliant legacy encryptors with new CryptoMod Standards. Customers have articulated the same problems about their current Type-1 Secure Conferencing systems: they are not ACC compliant; they suffer from poor voice quality; or they frequently do not work, forcing them to rely on another agency’s conferencing bridge.
Code Talkers: Transmitting messages in Choctaw

The need for secure communication is as old as tactical communication itself. When the US Army entered combat during World War One, the communications gear of the 1918 era was crude by today’s standards but still highly effective within the prevailing combat environment in France. German forces quickly developed ways to listen in on American tactical communications. In response, the Army leveraged a unique element of American culture and diversity to create a highly effective and uniquely American solution for secure tactical communication.
C2 comms in one platform: improving interoperability while lowering lifecycle costs

Today’s C2 communications are more complex and expensive than they need to be. All branches of the U.S. Military — and many coalition partners — are seeking next-gen technology to improve resiliency and mobility while simultaneously reducing costs and training time. REDCOM has always emphasized interoperability, ease of use, and flexibility. We built Sigma from the ground up based on these core tenets and to meet requirements for tactical users.