Push-to-talk (PTT) solutions currently employed within the DoD are complex, expensive, and challenging to maintain. The warfighter at the tip of the spear requires a powerful but easy-to-use solution that enhances current capabilities while minimizing cognitive overload. REDCOM technology increases the warfighter’s effectiveness and security posture while reducing lifecycle, training, and maintenance costs. Additional benefits include:
- Intuitive and simple GUI interface — minimizes ‘button presses’
- Perpetual licensing model — REDCOM software can still be used without annual maintenance agreements
- Integrated RoIP — reduces the complexity and cost to bring RoIP onto the command and control network by simplifying network architecture and eliminating additional hardware and software from the network
- Interoperability — mitigate obsolescence with hardware and software that are fully interoperable with existing deployed equipment
- Enhanced mobility — REDCOM solutions are incredibly easy to use, setup, configure, deploy, and are resilient to hard shutdowns
- Supports DOTMLPF-P Analysis — REDCOM technology is already included in the U.S. Army baseline and included in existing ATOs
The Current Problem
In voice communications, multiple hardware and software solutions are often cobbled together to provide critical capabilities. The result is a complex, increasingly hard-to-manage solution set, as each of these products must be procured, configured, tested, and documented. Subsequent upgrades require additional testing, compounding the effort required to maintain a multi-vendor solution. Advancements in technology often increase complexity and add to the cognitive burden of the warfighter. Furthermore, these multi-vendor solutions require extensive training and re-training of personnel and contractors in theatre, impacting operational readiness. This is notably expensive and time-consuming, especially with the personnel changes that occur regularly.
From a lifecycle management standpoint, some applications today only offer a subscription-based model. While beneficial to the manufacturer, this model leaves military customers vulnerable and increases sustainment costs with the number of software solutions required. From a security perspective, some applications in use today must utilize Microsoft Windows STIGs. A significant effort is necessary to adhere to these STIGs, which can delay delivery to the government and/or require the government to assume risk.
Recommendations
Choose a flexible, easy-to-use solution that converges capabilities onto one low-SWaP package tailored and scaled to mission-specific requirements. These capabilities include voice, video, chat, audio and video conferencing, transcoding, secure soft clients, console, and TSM integration.
This approach enables the end user to divest multiple pieces of hardware and software in use today, greatly reducing maintenance, lifecycle, training costs, and the warfighter’s cognitive burden. The solution should be standards-based to allow for the rapid insertion of new technology while ensuring backward compatibility with already fielded devices and systems. This increases interoperability.
Customers who wish to replace their existing voice+PTT management solutions have three courses of action (COA) available.
COA 1: REDCOM SIGMA® C2 SOFTWARE-ONLY SOLUTION
REDCOM Sigma® is an intuitive software-based command and control (C2) platform designed to increase operational flexibility while minimizing size, weight, and power (SWaP) requirements. With rapid boot time, quick setup, and resilience to hard shutdown, REDCOM Sigma delivers a fully scalable feature set, including voice, video, chat, conferencing, and an integrated C2 console.
Sigma Key Benefits
- Entirely software-based solution; hardware- and hypervisor-agnostic
- Flexible deployment options: Virtualized, CMOSS, Bare metal, and Cloud
- Works with already fielded RoIP gateways and SIP devices
- Removes expensive voice management solutions
- Scalable up to thousands of users
- Transport Agnostic
COA 2: REDCOM SIGMA® XRI-400
The REDCOM Sigma Extended Radio Interoperability (XRI-400) platform is a small form factor command and control (C2) platform that contains all of the capabilities of REDCOM Sigma software. The XRI-400 delivers voice, video, chat, and radio interoperability in a single low-SWaP ruggedized box, making it the perfect solution for all tactical echelons.
Sigma XRI-400 works with virtually any public safety or tactical radio, including portable radios, mobile radios, base stations, and repeater units, and it does not emit radio frequency radiation that might interfere with radios or other nearby electronic equipment.
Sigma XRI-400 Key Benefits:
- Maximizes cost savings by using one integrated, low SWaP box
- Removes expensive voice management solutions
- Works with existing gateways and, in many scenarios, can outright replace existing gateways
- Increases resiliency by enabling C2 comms even when disconnected from higher headquarters
- Increases operational flexibility by enabling the radios to be placed away from the TOC due to terrain
- Transport agnostic: works with any form of encryption, waveform, and transmission path
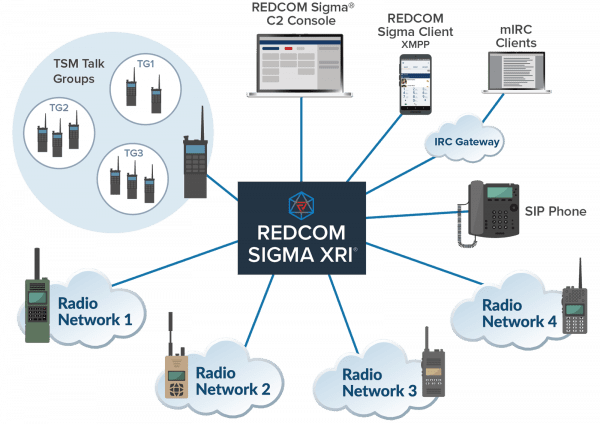
COA 3: REDCOM SIGMA XRI FUNCTIONALITY AS A MODULE IN A KLAS OR PACSTAR CHASSIS
We offer ALL of the Sigma XRI-400’s functionality in a module specifically designed for the Klas Voyager and PacStar Tactical Communication Systems. Capabilities include voice, video, chat, transcoding, radio gateway, radio interoperability, native TSM integration, conferencing, and Secure Clients for Windows and Android. Sigma can already work on these chassis with a third-party RoIP gateway, but with these modules, you eliminate additional third-party hardware while simplifying the network and reducing procurement, management, and sustainment costs.

A module for the Klas Voyager m-Series platform. Sigma software runs on a connected Klas compute module.

A module that fits into PacStar systems. Sigma software runs on a connected PacStar 400-Series server.
Key Solution Requirements
SIGMA® C2 CONSOLE
The REDCOM Sigma® C2 Console app offers a complete command and control (C2) management solution where a console operator can quickly establish connections and create persistent patches to facilitate immediate communication between various parties, even those with differing communication platforms. The C2 Console works with any reachable endpoint, including a SIP device, an analog phone over a SIP trunk, a radio voice net, or a talk group on a TSM mobile ad-hoc network (MANET).
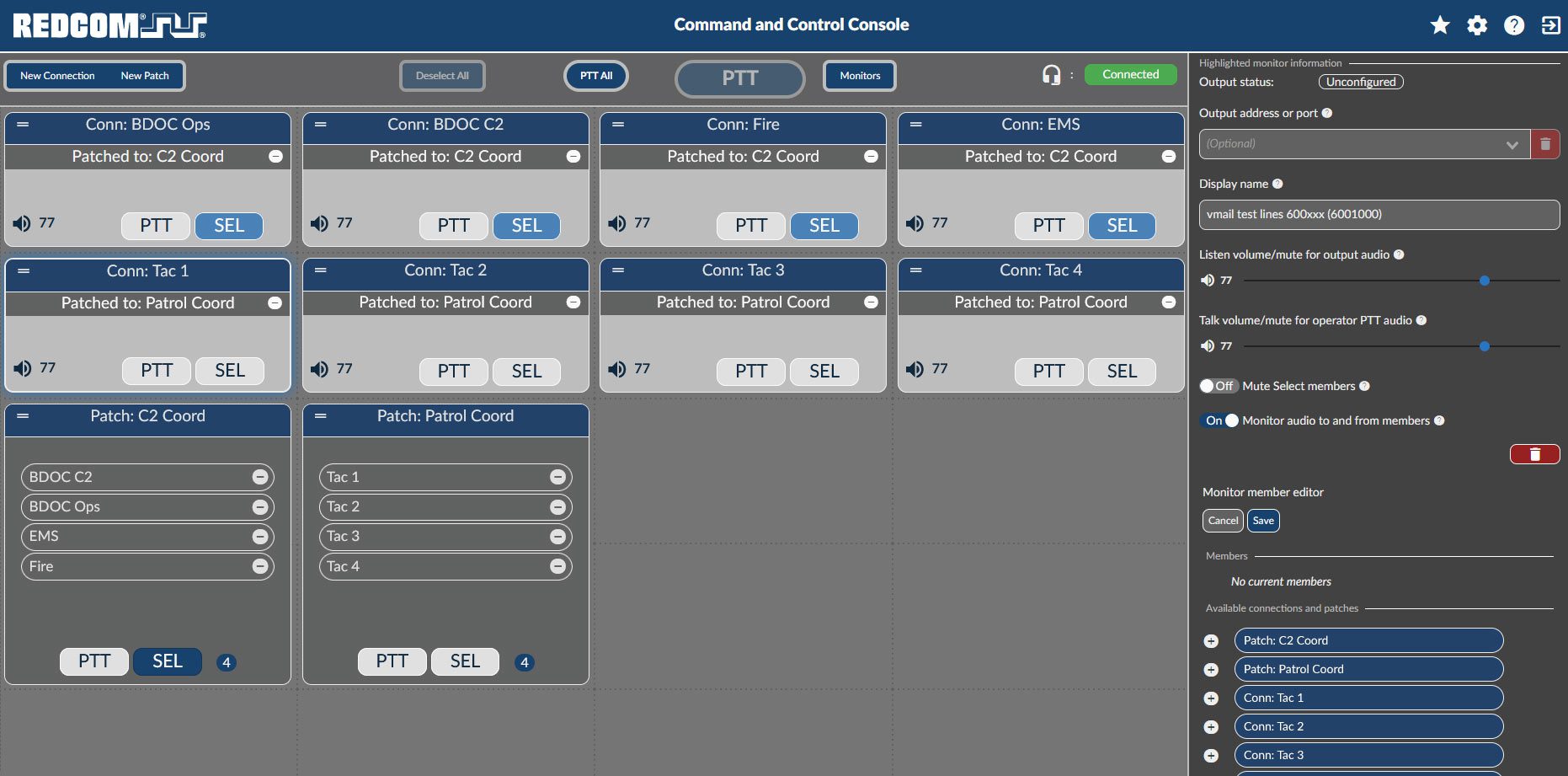
Using this app, console operators can create ad-hoc connections and patches, talk to a single connection or patch or a group of connections or patches using push-to-talk (PTT) functionality, and establish a listen-only path to any number of existing connections and patches. Console operators can also add connections and patches as members of monitor groups and select an output address or port to establish a listen-only path that continuously receives the combined audio from those members.
Auto Attendant
Auto Attendant is used to automatically distribute calls to phones, radio networks, or trunks based on user input. An automated greeting will be heard when a user dials the auto attendant code. The user can then dial 0-9, *, or #, and the call will be distributed accordingly. The greeting describes the options to the user.
TSM Integration
REDCOM Sigma includes native interoperability with TSM mesh networks, extending voice talk groups beyond the TSM network by linking them with other analog radios and the rest of the C2 network. A simple IP connection to a gateway radio is all that is needed for Sigma to access all of the talk groups on a TSM mesh network. Because each talk group is a virtual radio network, Sigma treats each talk group as its own independent radio net.
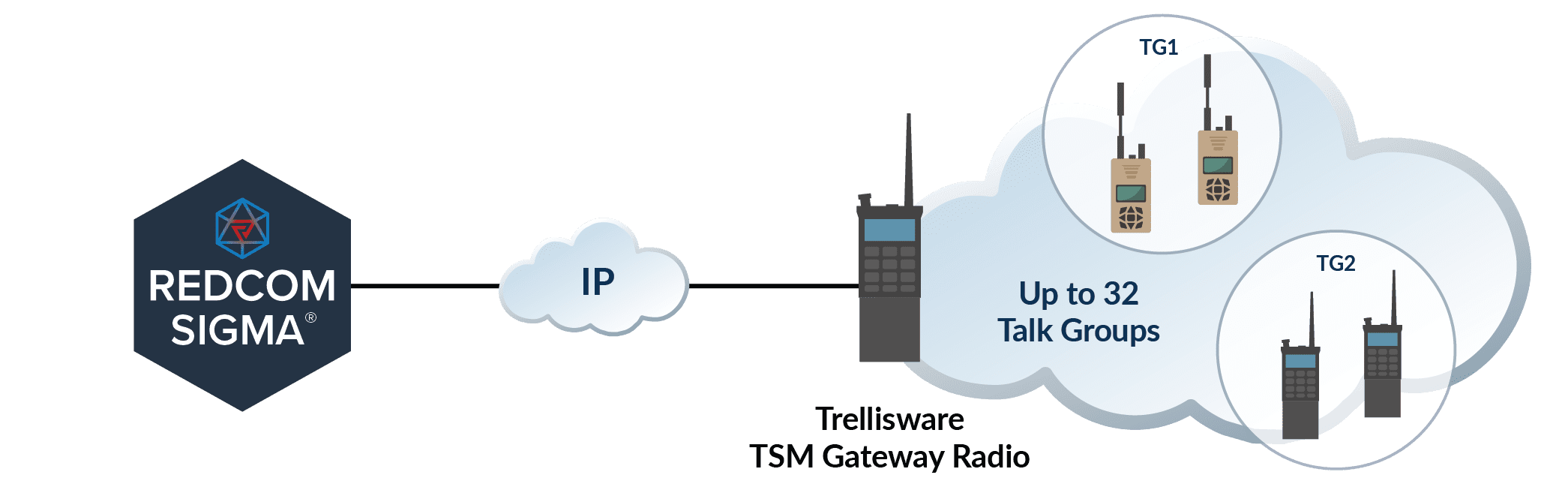
Simultaneous Sigma access to all non-classified talk groups.

Independent of TSM talk groups
REDCOM Sigma Client
The REDCOM Sigma Client is a softphone app for Windows® and Android™ that provides seamless, secure communications — including voice, video, and chat with presence — from the convenience of your PC, smartphone, and tablet.
REDCOM Sigma Client Key Benefits:
- Secure communications
- Push-to-talk (PTT)
- Full Multi-Level Precedence and Preemption (MLPP) support
- Intuitive user interface
- Dual registration
- Interoperability with industry-standard devices
- Chat functionality
- Sigma uses Extensible Messaging and Presence Protocol (XMPP) and offers an IRC gateway, allowing the Secure Client for Windows App to access both XMPP and IRC chat sessions within one app.
- Provides one chat interface for all phases of an operation and eliminates the need to jump from mIRC in planning to XMPP during execution. It also diminishes the need for a human relay and allows the ability to stay connected to the constant and critical coordination that takes place on mIRC during an operation. Jabber, Transverse, TAKchat, etc. all use XMPP.
- Chat panels can be resized, tiled, and moved around, with the most important panels placed where you want them. Unnecessary elements can be hidden to maximize space for chat panels.
- Users can flag individual chat messages sent as urgent. This highlights the chat message in red for both the sender and receiver.
- Users can tag chat rooms with keywords and key phrases to help certain messages stand out. The app supports local key phrases (unique to the end user) and room key phrases (set by the chat room organizer).
Security Posture
REDCOM Sigma includes built-in security prerequisites to simplify management and delivery while decreasing security risks.
- FIPS 140-2 validated with a roadmap for FIPS 140-3.
- Our software goes through thorough interoperability and cyber security testing to become certified as a Local Session Controller at JITC.
- We apply DISA STIGs to secure our systems and release a STIG guide for our customers.
- Each software version is scanned by a NESSUS Tenable scanner and compared to the CVE database to search for vulnerabilities. In both cases, vulnerabilities are promptly addressed and patched.
- Sigma meets the National Institute of Science and Technology Risk Management Framework checklist requirements. Sigma evaluated under FIPS 199, SP 800-37 Risk Management Framework establishes the risk of Sigma to “organizational operations, organizational assets, individuals, other organizations, and the Nation due to the potential for unauthorized access, use, disclosure, disruption, modification, or destruction of information or IT” as Low.
- REDCOM is Trade Agreement Act Compliant (TAA). All research, development, and manufacturing are conducted at REDCOM’s Victor, New York facility with 167 US Citizen REDCOM employees.
Operational Benefits
The Operational Benefits provided by this effort fall under three categories: reduction of lifecycle costs, sparing of resources, and increased resiliency:
- REDUCTION OF LIFECYCLE COSTS
REDCOM technology reduces lifecycle costs by providing a single platform solution that reduces licensing costs and minimizes support and training requirements. The DoD will reap significant cost savings through the change from the current batch annual licensing to a truly scalable perpetual licensing model. Due to the reduction of hardware and software, the government will reap additional savings by reducing the amount of required training and supporting documentation.
- SPARING OF RESOURCES
Resource sparing will be realized by reducing required contract support and Signal resources. The simplified REDCOM solution enables the system to be managed and maintained with organic resources within the unit. In addition to reducing the number of required Signal resources, REDCOM technology minimizes the need to bring contractor support into hazardous areas. REDCOM Sigma effectively spares resources and increases efficiency without impacting effectiveness or resiliency.
- INCREASED RESILIENCY
Resiliency is a key attribute for any system required for Operations and is realized through distributed management and redundancy. REDCOM Sigma software operating at higher levels is the same software that is used within the Sigma XRI-400 hardware. Due to this distributed architecture and redundant paths, control will be maintained regardless of the loss of communication paths.
REDCOM SIGMA ROADMAP
REDCOM will continue to build upon existing capabilities based on user feedback and requirements. Unlike our competitors, we will drive to implement these features based on direct feedback from our DoD customers.
C2 Console Enhancements:
Below is a general list of features we are looking to add to the C2 Console app:
- Softphone integration
- Chat within C2 Console UI
- More user role access
- Binaural audio with headset
- Operator-to-Operator communications
- Client-based variant of PTT console
- Remote radio control
- Voice recording
ATAK PLUG-IN
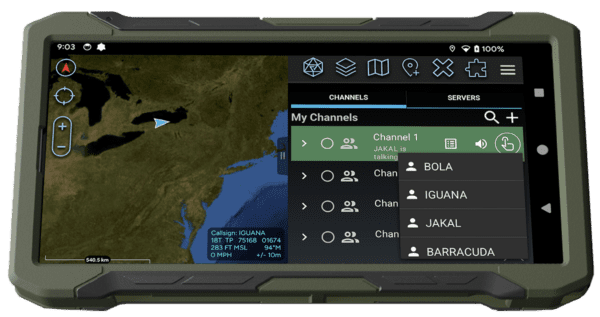 As of May 2024, we have completed the development of a new Console-like Push-to-Talk (PTT) Client application to mimic some of the critical capabilities described above in the C2 Console. The first iteration of this client is in the form of an ATAK plug-in that effectively merges two critical ecosystems within the Army: REDCOMs Sigma software and TAK. This new solution pushes more command and control/interoperability down to all end users carrying EUDs with the TAK application. Direct integration will allow users to communicate point-to-point or with multiple disparate devices simultaneously through pre-configured talk channels, all without switching applications. This Sigma TAK plug-in will also incorporate chat capabilities and bring existing Sigma Secure Client benefits like XMPP federation and an IRC gateway to TAK.
As of May 2024, we have completed the development of a new Console-like Push-to-Talk (PTT) Client application to mimic some of the critical capabilities described above in the C2 Console. The first iteration of this client is in the form of an ATAK plug-in that effectively merges two critical ecosystems within the Army: REDCOMs Sigma software and TAK. This new solution pushes more command and control/interoperability down to all end users carrying EUDs with the TAK application. Direct integration will allow users to communicate point-to-point or with multiple disparate devices simultaneously through pre-configured talk channels, all without switching applications. This Sigma TAK plug-in will also incorporate chat capabilities and bring existing Sigma Secure Client benefits like XMPP federation and an IRC gateway to TAK.
CMOSS
REDCOM’s claims of reducing lifecycle costs by offering a future-proof solution you’ll never have to rip and replace translate directly into the vision for CMOSS. We’ve built all of our products on open standards and will continue to do so in the future. This is why we can take our Sigma software (with no additional development), load it onto a CMFF 3U Open VPX CPU card, and have everything work. We can bring all the benefits described above directly into CMOSS and be the primary C2 communications platform within this architecture, providing interoperability where it is desperately needed the most. This eases the burden of transitioning to CMOSS and addresses the challenges of a widescale implementation head-on.
Distributed Control
Based on the enemy and environments in which our armed forces are prepared to fight, it is impossible to completely eliminate the risk of system downtime or loss of connectivity. In other words, no matter what technology is being used or where it’s deployed, connectivity problems are inevitable. REDCOM is committed to mitigating these issues as much as possible by leveraging distributed control. We can distribute multiple instances of Sigma throughout the network, with the ability to control all of them from a central point. Should the enemy take out one node, control will automatically shift to the next available instance of Sigma, sustaining critical communications at all times.
Zero-Trust Multi-Factor Authentication
REDCOM’s cybersecurity business unit, ZKX Solutions, has developed a patented Multi-Factor Authentication (MFA) solution that is more secure, dynamic, and flexible than conventional authentication options. ZKX provides peace of mind that I am who I say I am and prevents successful malicious attacks through a novel use of cryptography and a revolutionary approach to increase the cybersecurity posture while reducing friction for the end user in any environment. REDCOM is integrating ZKX technology into Sigma to introduce Zero Trust protections to the tactical C2 network that secures network resources while maintaining usability for end users. This technology will also make it easier for joint and coalition partners to operate within our C2 networks via next-gen Zero Trust policy enforcement and support Bring Your Own Device (BYOD) authentication around the globe.











