Introduction
The zero-trust architecture (ZTA) is a novel conception of network construction designed to eliminate the overall concept of “trust” from day-to-day network operations. Currently, security is traditionally relegated to the network’s perimeter: if access was granted to a specific user’s account, then that user is free to enjoy the privileges associated with said account. The ZTA security model eliminates the idea of trusted networks, devices, personas, or processes, and shifts to multi-attribute and multi-checkpoint-based confidence levels that enable much more granular authentication and authorization policies.
President Biden signed an executive order pertaining to cybersecurity on January 19, 2022. This executive order further emphasizes already laid-out security measures and gives agencies with national security systems 60 days to update agency plans to prioritize resources for the adoption and use of cloud technology, including the adoption of the Zero Trust Architecture.
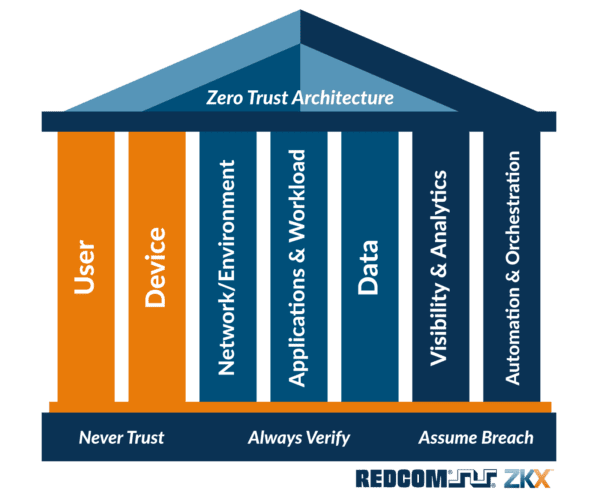
The momentum towards this executive order can be traced back to April 2021, when DISA and the NSA released a 163-page document on the DoD Zero Trust Reference Architecture. This document is quite expansive and a bit intimidating. Our cybersecurity team has reviewed it thoroughly, so you don’t necessarily have to (though you certainly should read pages 1-21 at a minimum). One of the most critical points discussed are the seven key pillars — or focus areas — to implementing a zero trust environment.
The seven pillars of a zero trust environment
- User: Securing, limiting, and enforcing person, non-person, and federated entities’ access.
- Device: Having the ability to identify, authenticate, authorize, inventory, isolate, secure, remediate, and control all devices.
- Network/environment: Segment (both logically and physically), isolate and control the network/environment (on-premises and off-premises) with granular access and policy restrictions
- Applications & workload: Applications and workloads include tasks on systems or services on-premises, as well as applications or services running in a cloud environment
- Data: Zero Trust protects critical data, assets, applications, and services
- Visibility and analytics: Vital, contextual details provide a greater understanding of performance, behavior, and activity baseline across other Zero Trust pillars
- Automation and orchestration: Automate manual security processes to take policy-based actions across the enterprise with speed and at scale
Where to start: identity and authentication
The two most critical pillars are the user and the device; this needs to be the starting point. “All roads lead to identity and authentication,” says REDCOM’s Collin Sweeney, Senior Cyber Security Researcher. “The words ‘Zero Trust’ say it all: you aren’t going to trust any entity inherently. A ruggedized rigid process by which users can prove their claimed identity to another party is necessary.” Therefore, the user and device are the two most critical pillars and the starting point of Zero Trust.
The Cybersecurity and Infrastructure Security Agency (CISA) claims identity is defined as an attribute or set of attributes that uniquely describes an Agency user or entity. The agency needs to ensure the correct users have the right access, which is done by verifying their identity. A similar process takes place for the device. The main difference is instead of verifying a user or entity it is the verification of hardware connecting to a network.
Not all pillars can be achieved within the same solution. If you inherently have no trust, you need a way to authenticate the users and devices on your network. You must walk before you can run and by starting with the user and device you are doing just that. In implementing a ZTA, the goal is to protect your most valuable Data, Assets, Applications, and Services (DAAS). The first line of defense is making sure no unauthorized user or devices has access. Therefore, all roads lead to identity and authentication.
REDCOM ZKX: the solution for user and device authentication
REDCOM is a leading voice in the conversation on actualizing a working Zero Trust Architecture for the tactical edge. REDCOM’s new disruptive authentication technology, ZKX™, offers seamless and frictionless multi-factor authentication designed to embody the foundational principles of zero-trust. This is done by its lightweight construction and intentional “bottom-up” philosophy — integrating the enterprise with the edge, not the other way around. The benefits of ZKX are:
- Authenticates user and their device simultaneously
- Protects personal data by not storing personal information
- No data is at risk if the endpoint device is compromised
- Interoperable with various network mediums such as satellite, RF radio frequency, and IP networks
- Can adapt to policy requirements
- Deployed following policies already outlined
- Confidence levels can be enhanced simply by continued challenging of a user’s identity, it is not all or nothing
For more information on ZKX watch our webinar and read our FAQ.
Conclusion
Not all pillars of Zero trust are achievable simultaneously. The user and device need to be authenticated before you can begin securing the other pillars. If unauthorized devices or users can access your network the network, data, and remaining pillars have all been compromised. REDCOM provides a solution to tackle the two most critical pillars without rip and replace thus reducing your network footprint.